Understanding the Different Layers of Security Attacks in OSI Model
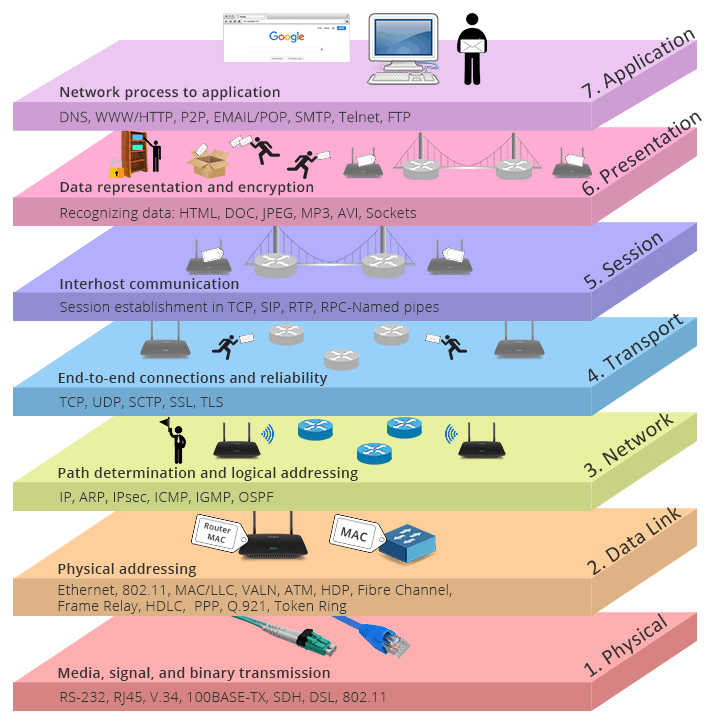
The Open Systems Interconnection (OSI) model is a framework used to standardize the communication process between networked devices. It consists of seven layers, each with a specific role in the communication process. However, each layer can also be vulnerable to different types of cyber attacks.
Physical Layer Attacks: At the physical layer, attackers can damage or disrupt network cables, wireless signals or other physical network components to disrupt communication.
Data Link Layer Attacks: The data link layer includes MAC address spoofing, denial-of-service (DoS) attacks and man-in-the-middle (MitM) attacks that intercept and modify network traffic.
Network Layer Attacks: IP spoofing, routing attacks, and Distributed Denial of Service (DDoS) attacks are examples of network layer attacks.
Transport Layer Attacks: Transport layer attacks can include SYN flooding, TCP reset attacks, and session hijacking that manipulate network connections.
Session Layer Attacks: Session layer attacks involve exploiting vulnerabilities in the session establishment process or hijacking active sessions to gain unauthorized access.
Presentation Layer Attacks: Presentation layer attacks exploit vulnerabilities in the data presentation layer and include SQL injection, cross-site scripting (XSS), and other forms of code injection.
Application Layer Attacks: Application layer attacks target vulnerabilities in specific applications. These attacks include web application attacks and phishing attacks aimed at stealing user credentials.
Understanding these different types of cyber attacks and where they can occur in the OSI model is critical for organizations seeking to secure their networks. By identifying potential vulnerabilities and deploying appropriate security measures, organizations can better protect their network against attacks and safeguard sensitive data.
In conclusion, cyber attacks can occur at any layer of the OSI model. It is essential to have a comprehensive understanding of these vulnerabilities to develop effective security strategies. Organizations must implement appropriate security measures to protect their networks and prevent data breaches.


No comment