A Comprehensive Framework For Understanding Automotive Cybersecurity Threats:
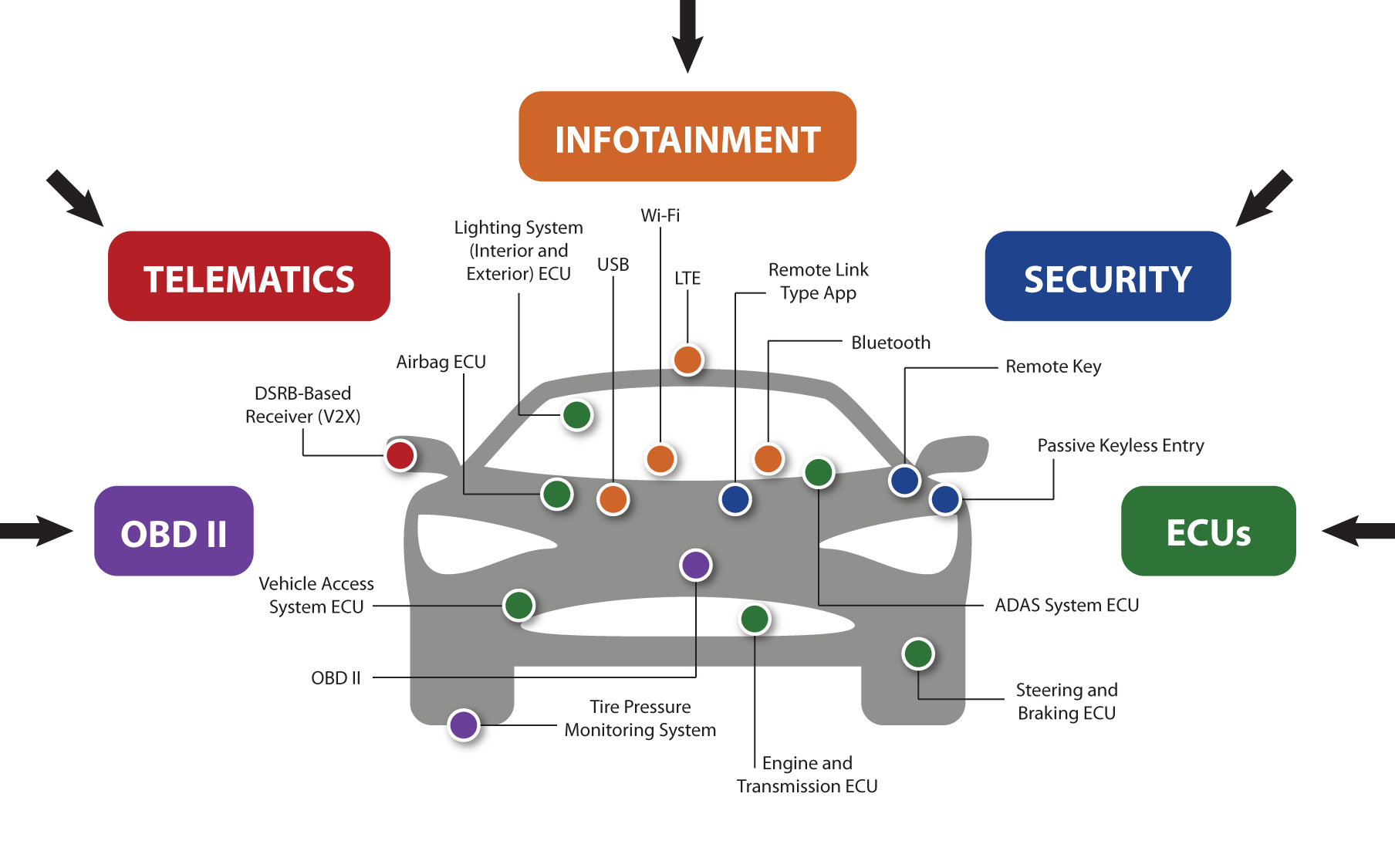
The increasing complexity and interconnectedness of automotive systems have led to a rise in cyber threats that can pose a significant risk to the safety and security of vehicles on our roads. As a result, it is crucial to conduct a thorough threat analysis and risk assessment to ensure that these threats are identified and addressed effectively.
One of the most comprehensive threat catalogs available is the Automotive Security Research Group (ASRG) threat catalog. This catalog is organized into a hierarchical classification system that helps users understand the nature of each threat and its potential impact on the vehicle ecosystem.
The catalog includes three main categories of threats: Primary Threats, Secondary Threats, and Tertiary Threats. Each category is further subdivided into subcategories that provide additional information about the nature of the threats.
Primary threats are the most significant threats that have the potential to cause the most harm to the vehicle ecosystem. They include physical access, firmware manipulation, and wireless attacks, among others. Secondary threats are still significant, but they are typically less severe than primary threats. Examples include data manipulation, replay attacks, and social engineering. Tertiary threats are considered lower risk, but they are still important to consider when conducting threat analyses and risk assessments. Examples of tertiary threats include denial-of-service attacks, side-channel attacks, and insider threats.
Each threat in the catalog is assigned a unique identifier, which can be used to reference the threat in discussions and documentation. Additionally, each threat includes a detailed description, along with information on potential attack vectors, impacts, and countermeasures.
The hierarchical classification system used by the ASRG provides a framework for understanding the relative severity of each threat and its potential impact on the vehicle ecosystem. By using this framework, organizations can prioritize their cybersecurity efforts and focus their resources on the most critical threats


No comment